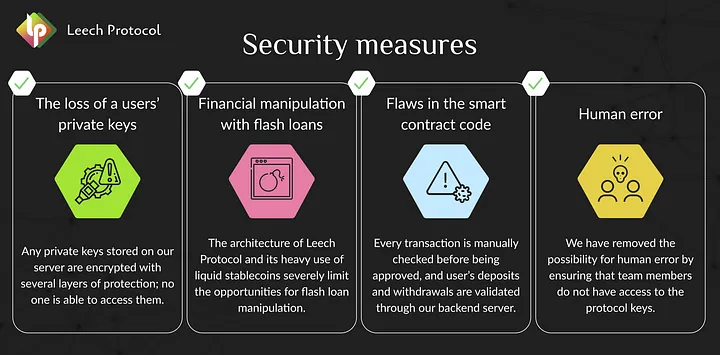
Yield Farming Academy #1 Crypto Wallets

This is the first lecture in the Yield Farming Academy section from the Leech Protocol. The path of any crypto enthusiast begins with the creation of a wallet. In this lecture we will tell you all about wallets and even more. Sit down comfortably, make yourself a cup of tea and we’ll start our tech journey!
Table of Content
- What is Crypto Wallet and how it works?
- The Evolution of Crypto Wallets
- Custodial and non-custodial wallets
- The public key & wallet address and private key & seed phrase
- Hierarchical Deterministic (HD) wallets
- How to Choose a Wallet
- Wallets Hacks
- Storing your seed phrase and private keys
- Our Experience and Video Example
What is Crypto Wallet and how it works?
A cryptocurrency wallet is like a digital safe that allows you to store, manage, and use your cryptocurrencies securely. It’s a tool that helps you interact with the exciting world of digital assets safely and conveniently. When you create a cryptocurrency wallet, you create a unique digital identity for yourself. It’s like having your own virtual bank account but with the benefit of complete control and privacy.
A critical aspect of a cryptocurrency wallet is the creation of your private and public keys. The private key is a confidential piece of information that only you should know. It’s like your secret password to unlock your wallet and make transactions. The public key, on the other hand, is like your public address. It’s what you share with others to receive funds.

What is Crypto Wallet and how it works?
Using a cryptocurrency wallet is as easy as using any other digital tool. Once you’ve set up your wallet, you can check your balances, send funds to others or receive funds. When you initiate a transaction, your wallet digitally signs it with your private key to prove that you’re the rightful owner of the funds. This signature is then broadcasted to the blockchain network, where it gets verified and added to the decentralized ledger.
This way, you can be confident that your transactions are secure and transparent. In addition, it’s impossible to reveal your private key from the signature. It’s important to note that different types of cryptocurrency wallets are available on the market. Some wallets are custodial, meaning they are provided by third-party services that manage your private keys on your behalf. Others are non-custodial, which means you have complete control over your keys and funds. Another critical point in understanding how wallets work is that your assets are not stored in a wallet, they are stored on a blockchain, and the wallet allows you to manage them.
With the right cryptocurrency wallet, you can dive into the exciting world of digital currencies and decentralized finance with confidence and peace of mind. Safely store your funds, manage your transactions, and explore the endless possibilities of crypto and the DeFi world. We created this session of Yield Farming Academy to describe all the essential aspects of crypto wallets. Please read it carefully and check our tutorial at the end. Also, we prepared some quests & tasks for you to prove your knowledge.
The Evolution of Crypto Wallets

The Evolution of Crypto Wallets
Crypto wallets have come a long way to cater the evolving needs of users and enhance security measures. Let’s explore the notable developments in the evolution of crypto wallets:
- Single-Currency Wallets: In the early days, crypto wallets were designed to support a single cryptocurrency. Users had to juggle multiple wallets if they held different types of digital assets. Examples of such wallets include Electrum, which focused on Bitcoin, and MyEtherWallet, tailored for Ethereum enthusiasts.
- Multi-Currency Wallets: As the crypto landscape expanded, wallets evolved to accommodate multiple cryptocurrencies within a single application. This consolidation made it more convenient for users to manage their diverse digital assets from one app. Popular multi-currency wallets include Exodus and Atomic Wallet.
- Mobile Wallets: With the rise of smartphones, mobile wallets emerged to provide on-the-go access to crypto management. These wallets enable users to send, receive, and store their digital assets from their mobile devices, ensuring convenience and accessibility. Trusted mobile wallets include Trust Wallet (available for iOS and Android) and Coinbase Wallet.
- Hardware Wallets: Recognizing the need for enhanced security, hardware wallets entered the scene. These physical devices store private keys offline, providing robust protection against hacking and malware. Ledger and Trezor are popular hardware wallet options renowned for their security features.
- Browser extensions: Wallets, also known as online wallets or DeFi Wallets, gained traction by offering wallet access from browser and interaction with decentralized apps on top of the web pages. MetaMask is a good example of browser extension wallet.
- Wallets with DeFi Integration: Some wallets have integrated decentralized finance (DeFi) capabilities, enabling users to interact directly with financial protocols and participate in activities such as yield farming and lending. This integration streamlines access to DeFi and enriches the user experience. Argent, and 1Inch Wallet are mobile wallets with DeFi features.
- Privacy-Focused Wallets: Privacy has become a growing concern for crypto users, leading to the emergence of wallets with enhanced privacy features. These wallets employ techniques like coin mixing, privacy protocols, and stealth addresses to boost transaction privacy and user anonymity. Wasabi Wallet and Samourai Wallet are prominent privacy-focused options.
- Cross-Platform Compatibility: Modern wallets are designed to work seamlessly across multiple platforms and devices, including desktop computers, mobile devices, and web browsers. This cross-platform compatibility enables users to access and manage their wallets effortlessly from different devices. Examples of wallets with cross-platform support include Exodus and Atomic Wallet.
By embracing these advancements, crypto wallets have evolved into sophisticated tools that empower users to securely store, manage, and transact with their digital assets.
Ultimately, choosing a cryptocurrency wallet depends on your needs and preferences. Consider security features, user-friendliness, compatibility with cryptocurrencies, DeFi interaction and backup options. Researching and selecting a reputable wallet that aligns with your requirements is always better than trusting someone’s opinion.
Custodial and non-custodial wallets
Custodial and non-custodial wallets are two different types of cryptocurrency wallets that differ in terms of control and custody of private keys.

Custodial and non-custodial wallets
Custodial Wallets: Custodial wallets, also known as hosted wallets or third-party wallets, are wallets where the private keys of the users’ cryptocurrency holdings are held and managed by a third-party service provider. In this type of wallet, users rely on the custodian to safeguard their private keys and manage their funds. Examples of custodial wallets include wallets provided by cryptocurrency exchanges like Coinbase, Binance, or Kraken.
Pros of Custodial Wallets:
- Convenience: Custodial wallets usually offer an easy setup process and a user-friendly interface, making them accessible to beginners.
- Password Recovery: In the event of lost passwords or keys, custodial wallets often provide assistance and mechanisms for users to recover their funds.
- Integrated Services: Custodial wallets offered by exchanges often come with additional features like trading or exchange functionalities, providing a comprehensive platform for users.
Cons of Custodial Wallets:
- Lack of Control: Users do not have direct control over their private keys as they are managed by the custodian. This means users are dependent on the custodian’s security measures and policies.
- Security Risks: Custodial wallets are more susceptible to hacking or internal breaches, potentially exposing user funds to risks.
- Privacy Concerns: Custodial wallets may require users to provide personal information and adhere to Know Your Customer (KYC) regulations, compromising user privacy.
Non-Custodial Wallets: Non-custodial wallets, also known as self-custody wallets or user-controlled wallets, are wallets where users have full control over their private keys. In this type of wallet, users generate and store their private keys locally on their devices or in a secure offline environment. Non-custodial wallets do not rely on any third-party service provider to manage the private keys or access the funds. Examples of non-custodial wallets include software wallets like Electrum, MetaMask, and Argent, or hardware wallets.
Pros of Non-Custodial Wallets:
- Full Control: Users have complete control and ownership of their private keys and funds. They are not reliant on any third-party custodian.
- Enhanced Security: Non-custodial wallets offer higher security as private keys are not exposed to the risks associated with third-party custodians.
- Privacy: Non-custodial wallets provide a higher level of privacy as user information is not shared with custodial service providers.
Cons of Non-Custodial Wallets:
- Responsibility: Users bear the responsibility of securely storing and managing their private keys. It is crucial to keep backups and protect against loss or theft.
- Recovery: Non-custodial wallets do not typically offer password recovery mechanisms. If the private keys are lost, recovery may be difficult without proper backups.
- Learning Curve: Non-custodial wallets may have a steeper learning curve for newcomers to the cryptocurrency space, as users need to understand private key management and security best practices.
When choosing between custodial and non-custodial wallets, users should consider factors such as security, control, privacy, and their own level of expertise in managing cryptocurrency wallets.
In our industry, we have amazing Quote.
Not Your Keys, Not Your Coins!
It is essential to weigh the trade-offs and choose the option that aligns with their preferences and requirements. We recommend using non-custodial wallets for most of the crypto portfolio.
The public key & wallet address and private key & seed phrase
Let’s dive into more technical aspects of the relationship between the public key & wallet address and private key & seed phrase:

The public key & wallet address and private key & seed phrase
Public Key: The public key is a publicly shared cryptographic key for encryption and verification. It is derived from the private key using a mathematical algorithm. Public keys are required to encrypt data or verify the authenticity of digital signatures. They are accessible to others without compromising the security of the encryption process. For example, when someone wants to send you an encrypted message, they use your public key to encrypt it. Only you, as the holder of the corresponding private key, can decrypt and access the message.
Wallet Address: A wallet address is a unique identifier used in cryptocurrencies to receive funds. It is a string of alphanumeric characters, such as a Bitcoin or Ethereum address. When you want someone to send funds to your wallet, you provide them with your address. The wallet address is derived from your public key using cryptographic algorithms. Therefore, it is convenient for others to send funds without knowing your public key, because the wallet address looks simpler than public key.
Private Key: A private key is a unique string of alphanumeric characters generated while creating a cryptocurrency wallet. This secret key grants access and control over the funds stored in the wallet. The private key is mathematically linked to a public key for receiving funds. To initiate transactions or access the wallet, the user must prove private key ownership. Safeguarding the private key is crucial because anyone with access to it can control the funds.
Seed Phrase (Mnemonic Phrase/Recovery Phrase): A seed phrase, or mnemonic phrase, is a set of typically 12, 18, or 24 words generated during the setup of a cryptocurrency wallet. It serves as a human-readable representation of the private key. In addition, the seed phrase acts as a backup or recovery mechanism for the wallet. It allows users to restore their wallets and regain access to their funds if they lose or forget their private key. The seed phrase is usually provided to users during the initial wallet setup and should be saved in a secure location known only to the owner.
The relationship between the public key**, wallet address, and the private key is interconnected.** The public key is derived from the private key, while the wallet address is derived from the public key.
Transactions are directed to the wallet address associated with the public key. The private key gives access and control to the address funds. The seed phrase serves as a backup for the private key, enabling wallet recovery if the private key is lost or forgotten.
It’s important to note that while the public key and wallet address can be openly shared, revealing the private key or seed phrase to others will compromise the wallet’s security and lead to unauthorized access or misuse of all assets.
Therefore, it is crucial to safeguard the private key and seed phrase, keeping them confidential and using them only in trusted environments.
Hierarchical Deterministic (HD) wallets
A few more technical aspects of wallet management. Believe us, it’s important to know. HD wallets are crypto wallets that allow you to manage multiple addresses and private keys within a single wallet. They generate a tree-like structure of keys from a master key or seed phrase.
When you set up an HD wallet, you’ll receive a seed phrase of 12, 18, or 24 words. This phrase serves as a backup for your wallet and can be used to restore all the keys in the wallet. From the seed phrase, the wallet algorithmically derives a master private key using the Hierarchical Deterministic key derivation algorithm. This master key acts as the root of the key hierarchy.
HD wallets
The key hierarchy is structured like a tree, with the master key at the top. The master key generates child keys, which can further generate grandchild keys, and so on. Each key is derived deterministically from its parent key using a specific path and mathematical calculations. As the keys are generated, corresponding crypto addresses are derived from the public keys. These addresses can receive funds or operate in DeFi.

The wallet software uses a key derivation path to determine specific keys for different purposes. Following the path, the wallet can generate other keys for different accounts or purposes while maintaining a deterministic relationship with the master key. With an HD wallet, you can manage multiple keys and addresses easily.
For example, you can generate new receiving addresses for each transaction or DeFi protocol, and the wallet will derive the corresponding private keys based on the hierarchical structure. To ensure backup and recovery, you must securely store the seed phrase. Then, if you lose access to your wallet, you can use the seed phrase to restore the entire key hierarchy and regain control over your funds.
MetaMask Wallet
HD wallets provide improved privacy and simplified backup with easy recovery processes. As a result, they have become widely adopted in the cryptocurrency industry for wallet management.
How to Choose a Wallet
When selecting a cryptocurrency wallet, it’s crucial to consider several factors to ensure security, functionality, and convenience. Here are some essential points to keep in mind:

How to Choose a Wallet
- Security: Prioritize wallets with robust security features such as encryption, two-factor authentication (2FA), biometric authentication, and integration with hardware wallets. Check the wallet’s security track record and whether it has undergone independent security audits.
- Type of Wallet: Choose between hardware, software, or web extension wallets. Hardware wallets offer the highest level of security by storing private keys offline. Software wallets can be installed on devices, while web extension wallets are accessible through browsers. Consider your security needs and convenience preferences.
- Supported Cryptocurrencies: Ensure the wallet supports the cryptocurrencies you intend to store or interact with. Some wallets support many coins and tokens, while others are more limited. Check the wallet’s documentation for a list of supported cryptocurrencies.
- Development Team and Reputation: Research the wallet’s development team and its reputation in the crypto community. Choose wallets developed by reputable companies or individuals known for maintaining and updating their wallets. Community reviews and feedback can offer insights into reliability and trustworthiness.
- Backup and Recovery: Check if the wallet provides a reliable backup and recovery mechanism. Ideally, the wallet should offer a seed phrase or recovery phrase that allows you to restore it.
- Additional Features: Consider any additional features or functionalities provided by the wallet. Some wallets offer integrated exchange services, portfolio tracking, staking, or other advanced features that enhance your crypto management experience.
- Community Support and Updates: Assess the wallet’s community support and frequency of updates. Active community support ensures prompt resolution of issues, while regular updates indicate active maintenance and improvement.
- Open-Source Nature: Open-source wallets allow the codebase to be audited by the community, adding transparency and security. If transparency and security are essential to you, use open-source wallets.
- Reviews and Recommendations: Look for reviews and recommendations from reputable sources or trusted individuals in the crypto space. Consider feedback from other users to gain insights into their experiences with the wallet.
Conduct thorough research and choose a wallet that aligns with your security preferences, functionality requirements, and user experience expectations. Always exercise caution, follow best security practices, and secure your wallet and recovery information.
Wallets Hacks
That’s why you should take your choice of wallet seriously! Here are some incidents where cryptocurrency wallets were compromised:

MyEtherWallet (MEW): In 2018, there was an attack on MyEtherWallet users through DNS hijacking. Hackers redirected users to a fake website that looked like a legitimate MEW site. The intention was to trick users into entering their private keys, leading to the theft of their funds. This incident highlighted the importance of verifying website authenticity and being cautious of phishing attempts.
Parity Wallet: In 2017, a vulnerability in Parity Wallet’s code allowed hackers to exploit multi-signature wallets and drain them of funds. This resulted in the loss of millions of dollars worth of ETH. The incident raised concerns about the security of smart contracts and the need for rigorous code auditing.
Ledger: In 2020, Ledger, a famous hardware wallet manufacturer, experienced a data breach. The breach exposed customers’ personal information, including email addresses and phone numbers. While the wallets’ security was not compromised, the incident raised privacy concerns and the potential for targeted phishing attacks.
Electrum Wallet: In 2018, the Electrum Bitcoin wallet was targeted in phishing attacks. Hackers set up malicious servers that displayed fake update notifications to users. When users downloaded and installed the fake update, they were prompted to enter their seed phrase, resulting in the theft of their funds.
These incidents highlight the importance of maintaining vigilance and adopting good security practices when using cryptocurrency wallets. It is crucial to download wallet software from official sources, keep wallets and software up to date, verify website authenticity, and be cautious of phishing attempts and social engineering tactics. Additionally, using hardware wallets, offline storage, and strong authentication measures can further enhance the security of your cryptocurrency holdings.
Storing your seed phrase and private keys
Safeguarding your seed phrase and private keys protects your crypto assets. Here are some recommended best practices:

Storing your seed phrase and private keys
- Offline Storage: Store your seed phrase and private keys offline whenever possible. Avoid keeping them on internet-connected devices like computers or mobile phones. Hardware wallets provide an excellent solution as they store private keys on a separate offline device.
- Hardware Wallets: Consider using a hardware wallet. These devices securely generate and store private keys offline, offering robust protection against hacking or malware attacks.
- Physical Security: Keep your seed phrase and private keys in a physically secure location, such as a safe or lockbox. Protect them from threats like fire, water damage, theft, or unauthorized access. Using tamper-evident bags or sealable containers can add an extra layer of protection.
- Multiple Copies: Create copies of your seed phrase and private keys and store them in secure locations. This helps mitigate the risk of losing access due to a single incident, such as theft or damage to one copy. However, be mindful not to create too many duplicates that could increase the risk of unauthorized access.
- Encryption: If you store your seed phrase or private keys digitally, encrypt them using strong encryption algorithms. Use reputable encryption software or hardware devices to safeguard your data. Encrypting the files adds a layer of protection if they fall into the wrong hands.
- Avoid Digital Storage: It is generally recommended to avoid storing your seed phrase or private keys in digital formats like plain text files or online storage platforms. Digital storage can be vulnerable to hacking, malware, or unauthorized access if not adequately secured. If necessary, consider using encrypted files or password-protected storage solutions.
- Memorization: If feasible, memorize your seed phrase, ensuring you can accurately recall it without the risk of forgetting or making mistakes. Memorization eliminates the risk of physical theft or loss but requires careful attention to detail and reliable remembering.
- Limited Exposure: Minimize the exposure of your seed phrase and private keys. Refrain from sharing them with others unless necessary. You will receive many phishing attempts or social engineering letters to trick you into divulging sensitive information.
- Regular Backups: Make regular backups of your seed phrase and private keys. This helps ensure you have up-to-date copies in case of loss or damage to the original storage. Test the backup process to verify that you can recover your wallet using the backup information.
Remember, prioritizing the security of your seed phrase and private keys is crucial. Take necessary precautions to protect them from theft, loss, or unauthorized access. It is essential to balance security and accessibility, finding a storage method that meets your needs while minimizing risks.
Our Experience and Video Example
Thank you so much dear Farmer for going through this lecture about wallets. Of course, we will express our opinions regarding what we use.
For cold cryptocurrency storage, when we use an address once a month to receive or send coins, we use a hardware wallet – Trezor or independent PC without internet connection.
We use Electrum, Exodus, and Trust Wallet when we need to make transactions once a week.
For daily work with DeFi and testing new projects, we use MetaMask and Trust Wallet.
Of course, most assets are stored on cold wallets and less on DeFi wallets.
Saving keys & seeds and making a recovery is an essential part of operating with cryptocurrency. We use open-source encryption tools like Paranoia to encrypt the keys.
Here is the video tutorial about creating a wallet and saving a seed phrase using encryption.
Blowfish is a symmetric key block cipher algorithm that was designed by Bruce Schneier in 1993 as an alternative to existing encryption algorithms at the time. It operates on fixed-size blocks of data and uses a variable-length key, making it suitable for a wide range of applications.
Blowfish is considered a secure encryption algorithm, but it is worth noting that it is an older algorithm and has been largely superseded by newer algorithms such as AES (Advanced Encryption Standard). AES is now widely adopted and recommended for use in most applications requiring strong encryption.
Thank you so much for reading this lecture, we’re happy to help you get started on your journey! Remember, the most important thing in crypto is to live as long as possible with assets in the game. Why? Because you will have more chances per unit of time to win your million 🙂
What should you do next?
*Try our automated cross-chain farming app (soon)
* Follow our Twitter for more DeFi and YieldFarming tips
* Join our Telegram for Daily Farming discussion
* Join our Discord to claim your roles and become early community member