How Leech Protocol Manages Security Issues: Security Deep Dive
Outside of regulatory issues, the biggest risk facing DeFi at the moment is smart contract risk, or security risk. When real value is involved, users need to have complete confidence in a protocol’s security to deposit money into it. As one of the premiere cross-chain yield aggregator services, Leech Protocol takes security very seriously, and here we will examine the measures the team has taken to ensure safety of funds in the protocol.
First, we analyzed 59 separate smart contract hacks. The team then documented the security vulnerability that resulted in each hack, so we could ensure Leech Protocol would not be defenseless against any of those attack vectors.
These vulnerabilities can be divided into four groups:
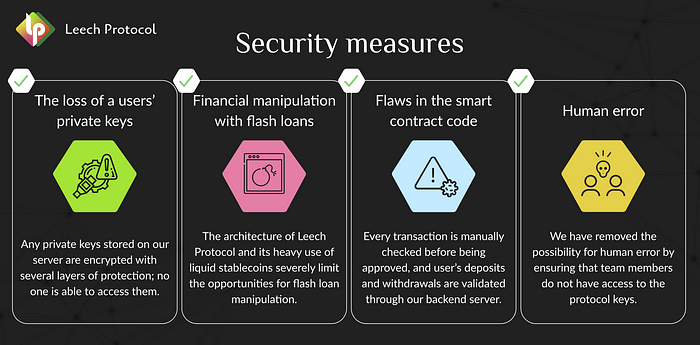
- The loss of a users’ private keys
- Financial manipulation with flash loans
- Flaws in the smart contract code
- Human error
For each of these groups, we established various security measures.
The loss of a users’ private keys
Any private keys stored on our server are encrypted with several layers of protection; no one is able to access them. Additionally, all funds are stored in liquidity pools, which each have their own deposit and withdrawal address that is hashed for added security.
Financial manipulation with flash loans
The architecture of Leech Protocol and its heavy use of liquid stablecoins severely limit the opportunities for flash loan manipulation. Additionally, when adding new tokens to the protocol, there will be a slight delay in the accrual of rewards, preventing manipulation of the protocol using flash loans.
Flaws in the smart contract code
Because using Leech Protocol involves interacting with smart contracts, we have established good security measures around them. Every transaction is manually checked before being approved, and user’s deposits and withdrawals are validated through our backend server. Reward accruals occur only once in a given period using an algorithm. This does not depend on the user, and prevents flash loan manipulation, as previously mentioned. Even if a hacker exploits a smart contract, they will not be able to steal users’ funds, as funds are stored at the addresses of a particular pool, not in the smart contract.
Human error
We have removed the possibility for human error by ensuring that team members do not have access to the protocol keys. As previously stated, all keys are fully encrypted on our server and not accessible by anyone.
Considering all of this, we are very confident in the security of Leech Protocol. We want to impress upon our community just how focused we are on our security since real value is involved, and how much attention we have given to it.
What should you do next?
- Provide liquidity via our farming App
- Follow our Twitter for more DeFi and YieldFarming tips
- Join our Telegram for Daily Farming discussion
- Join our Discord to claim your roles and become an early community member



